
Large language models are combining with artificial intelligence applications in cybersecurity to detect threats more effectively. In this content, explore the role and advantages of these...



Explore how the U.S. is ramping up efforts against Russian cyber operatives in response to the ongoing Ukraine conflict, focusing on cyber threats, national security, and...



Explore the intricate dynamics of cyber arms control, examining the challenges, strategies, and international efforts to manage the threats posed by cyber weapons in an increasingly...



Employees' personal activities can increase cybersecurity risks. In this content, explore the effects of individuals' private lives on workplace security and the measures that can be...



Explore the revelation of Iran's sophisticated hacking campaigns aimed at undermining U.S. elections. This in-depth analysis uncovers tactics, targets, and the implications for democracy in the...



Explore the far-reaching implications of the recent cybersecurity breach at National Public Data. Understand the risks to personal information, potential policy changes, and the impact on...



Cisco Systems has announced a 7% reduction in its workforce as the company faces declining earnings. This decision reflects the ongoing challenges in the tech industry...



Windows vulnerabilities allow cyber attackers to infiltrate systems. In this article, we will examine in detail how these vulnerabilities are exploited and the Downdate attack method.



DARPA's TRACTOR Project accelerates software development processes by facilitating the code conversion from C language to Rust language. This innovative approach contributes to modern software engineering...
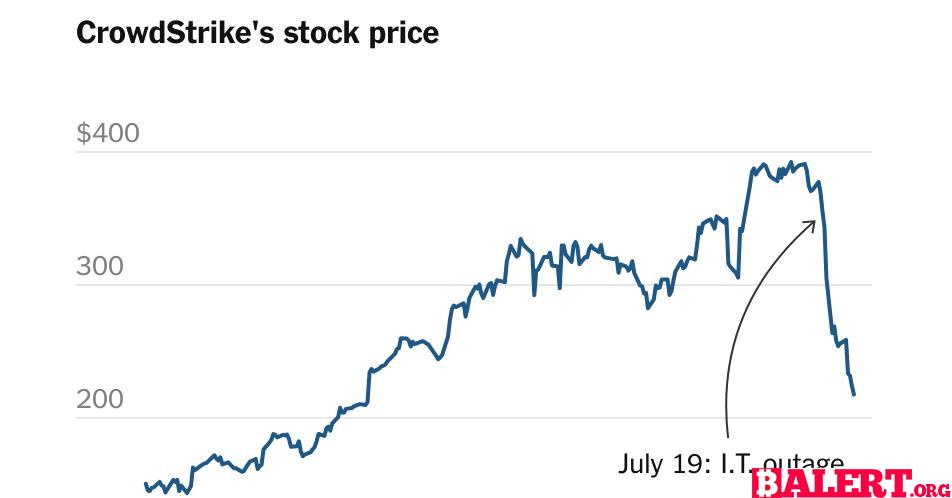
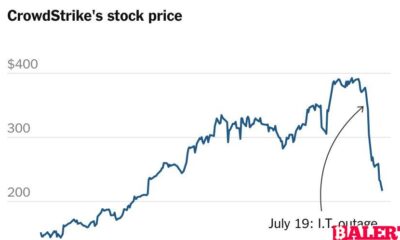
Explore the escalating legal battle between CrowdStrike and Delta Air Lines following a significant IT outage. Discover the implications for both companies and the tech industry...